Common Types of Scams
Phishing is when scam artists send official-looking emails, attempting to fool you into disclosing your personal information — such as user names, passwords, banking records or account numbers, or social security numbers — by replying to the email or entering it on a phone website. Phishers can pretend to be from a legitimate bank, organization, government agency, or store, or claim to be the host of a lottery or contest. Some even imitate the University’s IT Help Desk.
Report phishing, whether you have become a victim or not. Tell the legitimate company that a phisher was impersonating them. If you were phished on a University computer or network, or if you believe your University account information was compromised, contact abuse@rochester.edu immediately (please see, instructions on reporting suspicious emails).
Also report the problem to the National Fraud Information Center and Internet Fraud Watch at www.fraud.org or 1-800-876-7060. Your report can prevent other people from becoming victims.
Higher Education is a popular target for employment scams – fake emails that appear to come from University officials or faculty members promising too good to be true opportunities, enticing compensation and immediate hiring. While students are the primary victims, faculty and staff are also at high risk (research opportunities, etc.).
This email claims to be from the Vice President for Research and Chief Research officer. The message shows the need to fill the position immediately and will hire anyone who applies first. This is a red flag. The email also shows [EXT] in the subject line indicating the email is not coming from an internal University of Rochester email, but rather externally from an unknown sender and encourages the recipient reaches out to the Vice Dean for Research through a gmail account- another red flag!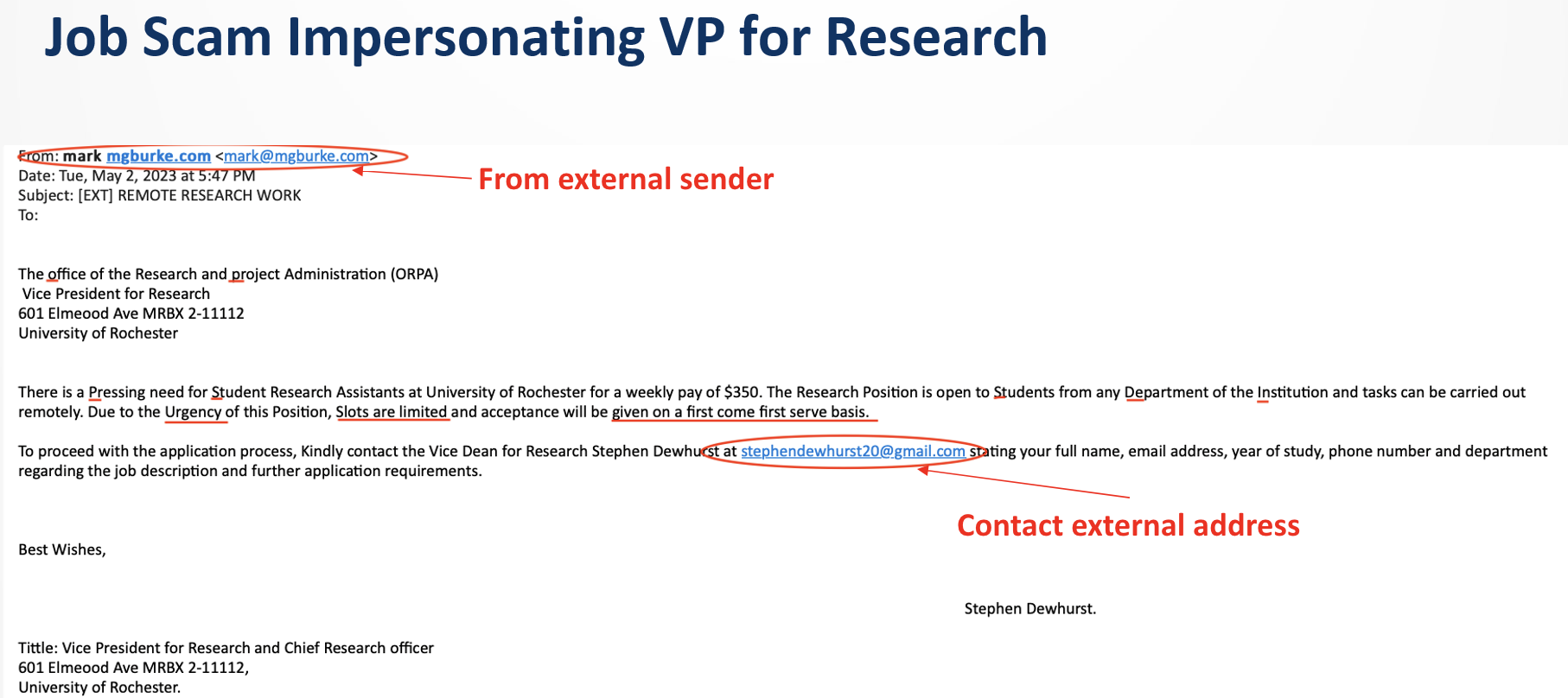
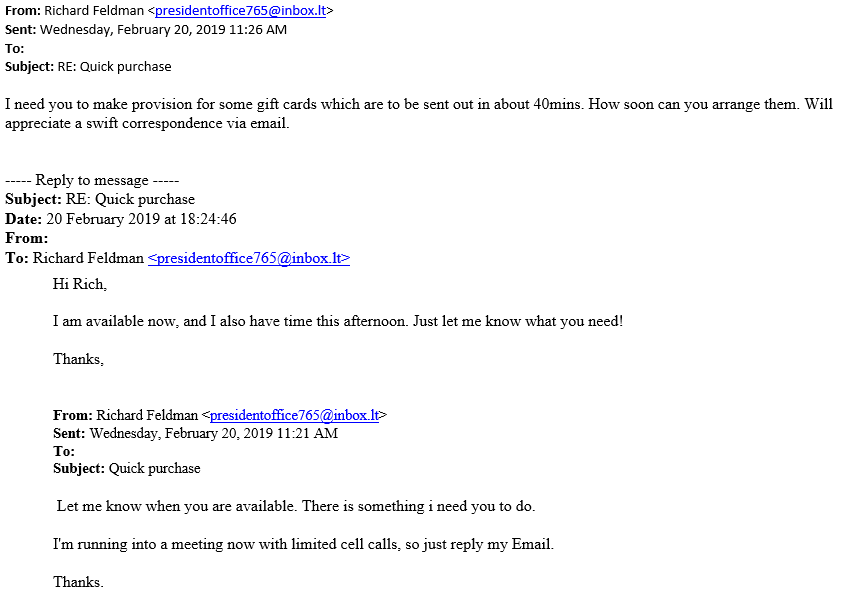
Before fulfilling any requests, you should validate that the sender is indeed who they say they are. This email appears to be from the University’s president, Richard Feldman. However, if you look closely, you’ll see the email address is not an official University of Rochester alias. If you’re unsure, report it immediately to abuse@rochester.edu
Pharming is when hackers install malicious code on a personal computer or server, which redirects clicks you make on a website to another fraudulent website without your consent or knowledge.
This is essentially the phone version of phishing, where callers try to trick you into providing information about your accounts over the phone.
Smishing attempts primarily use texts to lure you in with messages often requiring immediate attention, or directing you to a malicious URL.
Quishing involves the use of fake QR codes [containing malware or directing users to malicious sites] and placing them in public places for individuals to scan.
How to Protect Yourself from Scams
- Be on the lookout for suspicious emails or text messages. Legitimate, responsible companies will never solicit personal information over email. Never reveal personal or financial information in response to an email request, no matter who appears to have sent it.
- Don’t click on links or attachments in suspicious emails or text messages. Instead, visit the mentioned website directly by using a search engine to locate the real site. If the web address listed by the search engine and the address in the email do not match, the email is most likely a phishing attempt or spam, and you should delete it.
- Set up a spam filter. A spam filter can greatly reduce the amount of phishing emails you receive. University IT provides free spam management for University email.
- If you are still tempted to click, pick up the phone instead. If the message looks real and you are really tempted to respond, instead look up the phone number of the company and call them. Do not use any phone number in the email because it could be fake. Ask if the message was actually sent by the company and if you can take care of any issues over the phone instead.
- If you think you’ve received a suspicious email, forward to abuse@rochester.edu.
- Please see Suspicious Email Forwarding Instructions for additional guidance.
Identity Theft
Identity theft occurs when someone uses your name, Social Security number, credit card number, or some other piece of your personal information for financial gain. Thieves often use this information to apply for a credit card, make unauthorized purchases, gain access to your bank accounts, or obtain loans under your name. The Federal Trade Commission estimates that as many as 9 million Americans have their identities stolen each year.
How to Protect Yourself from Identity Theft
- Shred and destroy unwanted documents that contain personal information, including mail, unwanted credit card offers, old bills, etc. Cut up your expired or unwanted credit cards.
- Bring your mail in daily — don’t leave mail in your mailbox. Have the post office hold your mail when you go on vacation.
- Don’t carry your social security card or birth certificate with you. Keep them locked up in a safe place.
- If a trustworthy group asks to use your social security number as an identifier, ask if something else may be used instead.
- Share personal information over the phone or online only when you are certain that you know the person or business with whom you’re speaking.
- When online, always review privacy policies, check the reputation of online organizations, and make sure your transactions are secure.
- Sign all new credit/debit cards as soon as you get them. If they are unsigned and end up lost or stolen, anyone can forge your signature on there instead.
- Be aware and note when your monthly financial statements arrive in the mail. Notify your financial institutions if they don’t arrive when expected.
- Carefully check your financial statement every month. If you spot suspicious activity, immediately inform your bank.
- Take all receipts with you after all credit/debit or ATM transactions. They contain at least part of your account number.
- Immediately report lost or stolen credit/debit cards and blank or incomplete checks.
- Watch your credit card expiration dates. If you don’t receive a replacement card before the expiration date, call the issuer.
- Create strong passwords.
- Keep all of your passwords secret and remember them without writing them down.
- Cover the screen with your hand when you type in your PIN at the ATM or cash register. “Shoulder surfers” will try to watch over your shoulder to steal your PIN.
- Keep your antivirus software and other software up-to-date to prevent hackers from stealing your personal information.
What to Do If You Think Your Identity Has Been Stolen
1. Immediately place a fraud alert on your credit reports.
- Equifax
Direct Line for reporting suspected fraud: 800-525-6285
Fraud Division
P.O. Box 740250
Atlanta, GA 30374
800-685-1111 / 888-766-0008 - Experian
Direct Line for reporting suspected fraud: 888-397-3742
Credit Fraud Center P.O. Box 1017
Allen, TX 75013
888-EXPERIAN (888-397-3742) - Trans Union
Direct Line for reporting suspected fraud: 800-680-7289
Fraud Victim Assistance Department
P.O. Box 6790
Fullerton, CA 92634
Phone: 800-916-8800 / 800-680-7289
2. If your Social Security Number has been stolen, contact the Social Security Administration (SSA) Fraud Hotline. The SSA can provide information on how to report the fraudulent use of your number and how to correct your earnings record.
- Social Security Administration
SSA Fraud Hotline: 800-269-0271
3. Close accounts that were accessed or opened fraudulently.
- Change the passwords on all of your accounts. Create a new, strong password — don’t reuse an old one or one that’s similar.
- File a report with the local police.