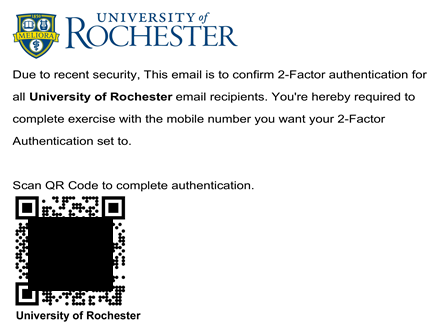
There has been a recent uptick of fake QR code phishing (also known as quishing) emails sent to the UR community. Quishing, is a type of phishing attack that uses QR codes (Quick Response Codes) to trick victims into revealing sensitive information or downloading malware. The UR community must be extra mindful of incoming emails where QR codes are present and avoid engaging or using their personal device to scanning an image of the code as this can install harmful malware to your device or steal your credentials. Although the Information Security team can block the malicious website from being accessed on the UR network, they cannot always monitor when quishing codes are scanned on a phone.
What is QR code phishing (quishing)?
QR code phishing, also known as quishing, is a type of phishing attack that uses QR codes (Quick Response codes) to trick victims into revealing sensitive information or downloading malware. Scammers can use QR codes in various ways, including:
- Emails and text messages: Unsolicited emails or texts with a QR code and a message urging you to scan it for security reasons, receiving a discount, a contest entry, or other seemingly beneficial reason.
- Social media: Malicious posts on social media platforms with a QR code and a misleading caption.
- Physical locations: QR code stickers placed on products, ATMs, or in public spaces could lead to fake login pages or malware downloads.
How does QR code phishing work?
When you scan a QR code with your smartphone camera or a QR code scanning app, it redirects you to a website or downloads a file. In a quishing attack, the QR code leads to a malicious website that looks like a legitimate one, such as your bank’s login page or a popular online store. Once you enter your login credentials or any other personal information on the fake website, the scammer steals it.
QR code phishing can also be used to download malware onto your device. This malware can steal your data, track your activity, or even take control of your device.
How to protect yourself from QR code phishing:
- Be cautious of unsolicited QR codes: Don’t scan QR codes that you receive in unexpected emails, text messages, or social media posts.
- Verify the source: If you see a QR code in a public place or from a company you know, contact them directly to confirm its legitimacy before scanning.
- Inspect the URL before scanning: Many QR code scanning apps allow you to see the URL encoded in the QR code before you visit it. Review the URL carefully for misspellings, unusual characters, or a different domain name than what you expect. Legitimate URLs should start with “[https://]” (note: the “s” in https verifies the site is secure) and use the correct domain name of the website you expect to visit (e.g.,”https://www.rochester.edu/“).
- Don’t enter sensitive information on unknown websites: The University and legitimate companies will never ask you to enter your login credentials or other sensitive information by scanning a QR code.
- Use a QR code scanner app with security features: Some QR code scanner apps can warn you about suspicious URLs or malware before you click on them.
- Keep your software up to date: Regularly updating your phone’s operating system and security software helps protect against vulnerabilities that scammers might exploit.
What to do if you receive a Quishing email:
If you receive an unexpected message like this, do not respond and delete the message after reporting it to abuse@rochester.edu. Instructions on forwarding messages can be found here.
What to do if you think you’ve been a victim of QR code phishing:
- Change your passwords immediately: If you entered your login credentials on a fake website, immediately change your passwords for all affected accounts.
- Scan for malware: Use your antivirus software to scan your device for malware.
- Report the attack: Report the phishing attempt to the platform where you encountered the QR code (e.g., social media platform, email provider) and to relevant authorities.
Recent example of a fake QR code attempt: