
WHAT IS PHISHING?
Phishing is when scam artists send official-looking emails, attempting to fool you into disclosing your personal information — such as user names, passwords, banking records or account numbers, or social security numbers — by replying to the email or entering it on a phone website. Phishers can pretend to be from a legitimate bank, organization, government agency, or store, or claim to be the host of a lottery or contest. Some even imitate the University’s IT Help Desk.
HOW CAN I IDENTIFY MALICIOUS E-MAILS?
- Identify the Sender. Do you know this person? Were you expecting e-mail from this person or does it fit in with your job role? If not, it is probably suspicious. If the email appears to come from someone you know or within your organization, double check the sender’s email address to be sure it matches correctly.
- Example: If an email message is claiming to be Dr. John Smith at URMC, but the email address is drjohnsmithURMC@gmail.com, this is a red flag!
- Look for [EXT]. If you see [EXT] in the subject line – BE CAUTIOUS! This means the email is an external email message coming from someone outside of the University of Rochester, URMC or UR Medicine. Click here for more information on external [EXT] emails.
- Reply-to. If the Reply-to address is different from the sending address, this should raise your suspicion for the whole message.
- Links and Attachments. If you were not expecting an attachment or a link, and you do not know the sender, do not open it! If you are not sure, check with the sender by phone (don’t use a phone number in the e-mail), otherwise report it.
- Grammar and Tone. With the use of AI technology, grammar and tone are becoming less prevalent in phishing emails and should not be your only source of truth to identifying a fake email. However, should you notice any grammar mistakes, suspicious language or tone that doesn’t appear typical of your colleagues- that is quick red flag.
- Emotions. Be wary of any e-mails trying to cause certain emotions. The most commonly-used malicious emotions are:
- Greed. Messages offering or promising you money by clicking a link or giving away information are usually.malicious. If it seems too good to be true, it probably is.
- Urgency. Unusually short deadlines create a false sense of urgency to act. Attackers employ this technique inattempts to confuse the recipient.
- Curiosity. Attackers take advantage of our curiosity by promising something exciting or prohibited content.
- Fear. Threatening recipients with negative consequences is a common tactic to generate responses—things suchas threatening to shut off accounts or legal action.
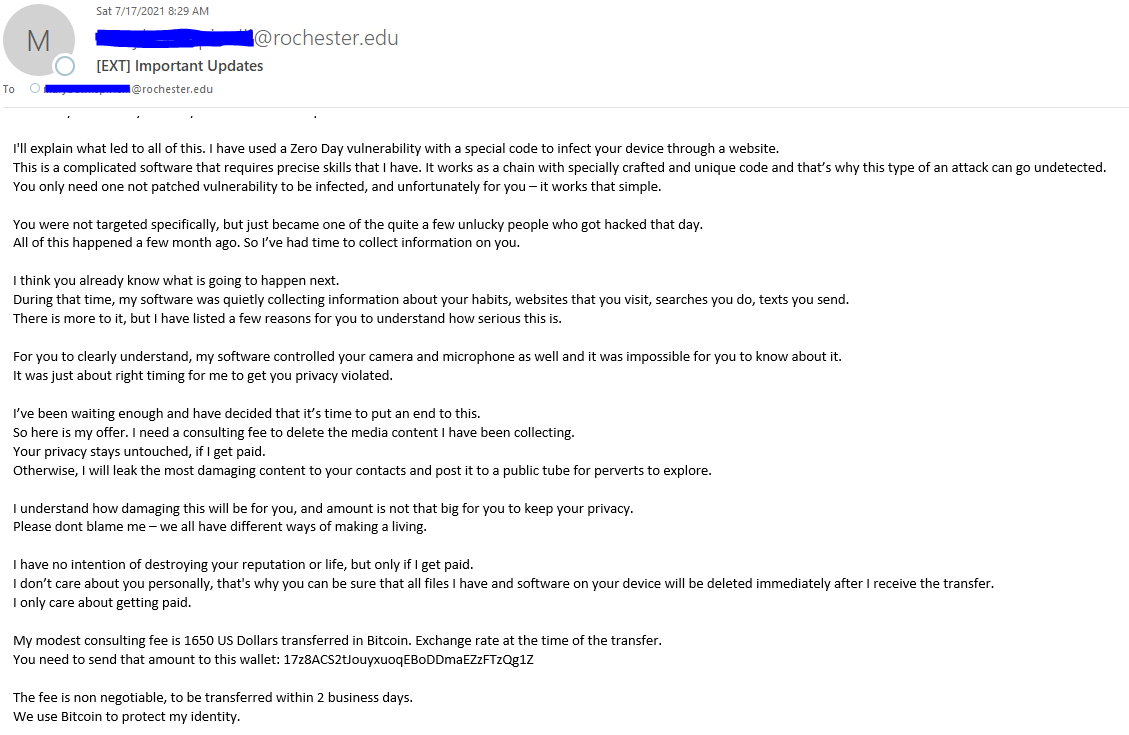
A University of Rochester employee received a letter attachment from a scammer trying to coerce them into paying Bitcoin in order to avoid the scammer exposing embarrassing and explicit photos/videos. This was fake, but the scammer was trying to use fear tactics by telling the victim they knew they’re phone number, home address and even a picture of their home (from google maps) so the victim fall for their tactics and pay.
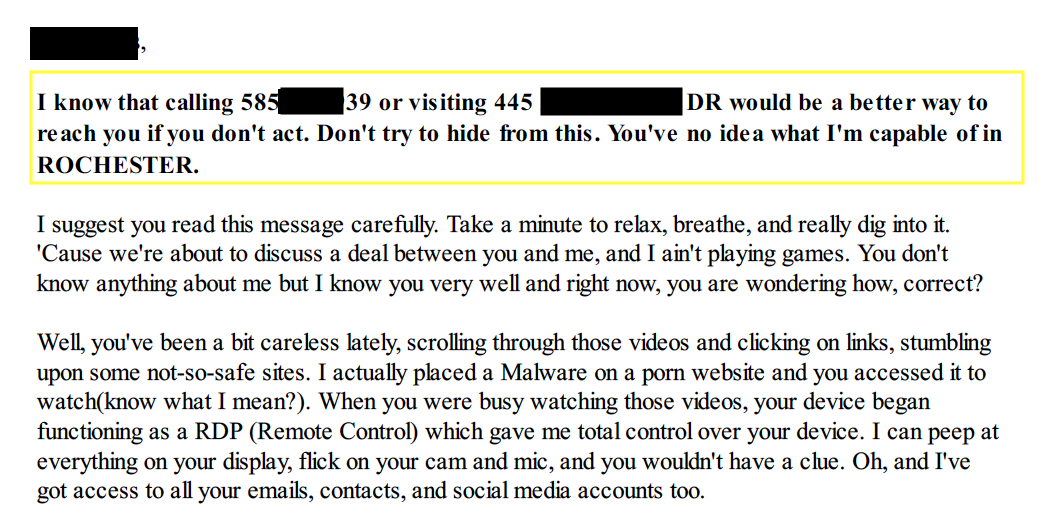

Below is a screenshot of a sextortion email scam that has been targeting University students, faculty, and staff lately. These scammers do not have any control of your computer or mailbox and are merely spoofing the sender email address in an attempt to induce fear in hopes of extorting you into reacting quickly and paying. You can simply delete the email from your mailbox.
Before fulfilling any requests, you should validate that the sender is indeed who they say they are. This email appears to be from the University’s president, Richard Feldman. However, if you look closely, you’ll see the email address is not an official University of Rochester alias. If you’re unsure, report it immediately to abuse@rochester.edu.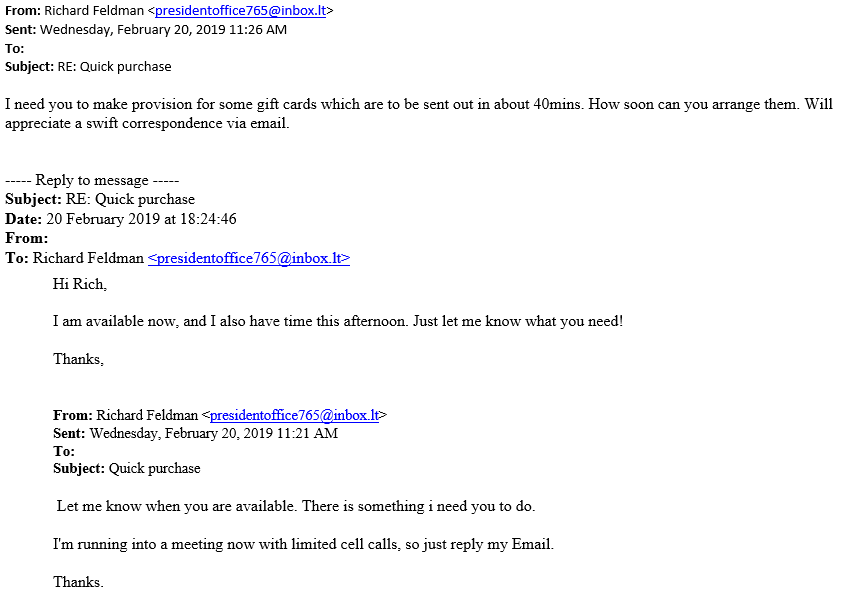
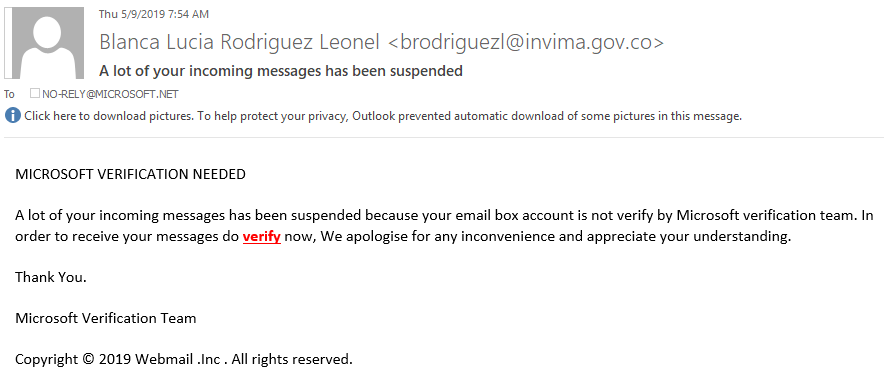
The email below appears to be from an official Microsoft team associate stating the suspension of incoming messages in an attempt to get victims to click links. If you mouse over any links, you can see the url and its true destination. Do not click the links in the email and always verify the sender- If an email is being sent by a reputable company, chances are their email will show affiliation. Also, notice below the grammatical errors which are signs that an email is fraudulent.
TIPS TO AVOID A PHISHING SCAM
- Be on the lookout for suspicious emails or text messages. Legitimate, responsible companies will never solicit personal information over email. Never reveal personal or financial information in response to an email request, no matter who appears to have sent it.
- Don’t click on links or attachments in suspicious emails or text messages. Instead, visit the mentioned website directly by using a search engine to locate the real site. If the web address listed by the search engine and the address in the email do not match, the email is most likely a phishing attempt or spam, and you should delete it.
- Set up a spam filter. A spam filter can greatly reduce the number of phishing emails you receive. University IT provides free spam management for University email.
- If you are still tempted to click, pick up the phone instead. If the message looks real and you are really tempted to respond, instead look up the phone number of the company and call them. Do not use any phone number in the email because it could be fake. Ask if the message was actually sent by the company and if you can take care of any issues over the phone instead.
- Change your passwords regularly. Whether or not you’ve fallen victim to a suspicious email, it is best to practice safe security by changing your password on a regular basis. Unlike keys or an ATM card, your password does not have to be physically taken to be copied, and it’s unlikely you’ll know when your password has been stolen. Visit University IT’s passwords page for tips to creating a strong password.
HOW CAN I REPORT SUSPICIOUS E-MAILS?
All URMC and Affiliates workforce members who receive suspicious e-mail should report it immediately to abuse@rochester.edu. Even if you are not sure, it is better to have the message checked first. In addition, just because you may think it is obviously bad, you should still send it along for analysis. What might be obvious to you may not be to another individual. Remember, if you see something suspicious, report it!
If you are using an ISD-managed computer, there is also another way to report suspicious e-mails. In your MS Outlook client of your computer, there has been a button added on the Home ribbon to the far right titled “Manage Unwanted.” If you click this button, you can select the option to “Report as Suspicious.” Doing so will send the message to the appropriate teams for evaluation.
HOW CAN I MAKE SURE MY MESSAGE LOOKS LEGITIMATE?
Several actions will help make your messages look legitimate.
1. Use links to sites with “https://” This directs your recipients to websites that can be verified by a trusted third party.
2. Offer alternatives to clicking the link. Give directions such as “Go to the Intranet, click on …”
3. Have direct contact information. Give your recipients a point of contact to verify the authenticity of the message.
4. Avoid attachments. Where possible avoid sending attachments. Try to use departmental file shares or other methods of file transfer.